As I am sure you are aware, the CMMC Proposed Rule came out the day after Christmas and has created a buzz of activity across the industry—both good and bad. The good news is all those people that made bets saying that CMMC would eventually come to fruition can now cash in their winnings. The bad news is there is a lot of misinformation being thrown around that’s causing confusion. Let’s reference a couple CMMC fictions that I’ve seen recently.
CMMC 2.0 rules lift burdens on MSPs?
If we’re going to spread the news, then we may as well get it all out there. Two things happened over the holiday break. One of those was the CMMC Proposed Rule being released and the other was the public release of the DoD Memorandum of FedRAMP Moderate Equivalency. Let’s pull that string a little and see if the proposed rule lifts the burden or more clearly defines the requirements.
Under the proposed rule there are two (2) terms that an MSP may fall under:
1) Cloud Service Provider (CSP) – means an external company that provides a platform, infrastructure, applications, and/or storage services for its clients. – CISA Definition
2) External Service Provider (ESP) – means external people, technology, or facilities that an organization utilizes for provision and management of comprehensive IT and/or cybersecurity services on behalf of the organization. In the CMMC Program, CUI or Security Protection Data ( e.g., log data, configuration data), must be processed, stored, or transmitted on the ESP assets to be considered an ESP. – CMMC Custom Term
I don’t know about you, but most of the MSPs I know don’t host client data in their own datacenters anymore. Instead, they outsource the hosting onto platforms like Microsoft and AWS and charge you for it. For those that do hose client data, the FedRAMP equivalency memo will be of great interest if they don’t already have an Authority to Operate (ATO).
For the low low price of 100% compliance with FedRAMP, ongoing operations tests, and annual/ongoing 3PAO engagement costs to name a few items you too can be considered FedRAMP equivalent. In case you missed the sarcasm, this is not a realistic goal for most organizations which leaves the ESP route.
So, you want to be an MSP but don’t think you fall into the category of an ESP? Let’s walk over to the current CMMC L2 scoping guide and see what they say is an example of a security protection asset (SPA), which also consists of ESPs (just so we’re tracking).
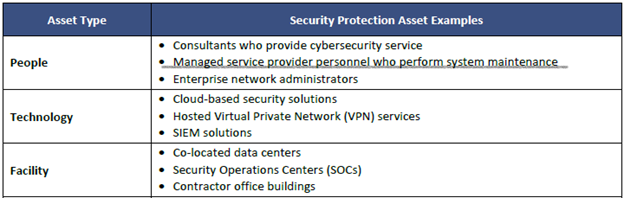
Well, looky here. Does your MSP provide maintenance to your systems? What about managing your log data, workstation builds, users, etc.? Regardless of if they want to argue that they’re not processing, storing, or transmitting CUI data, they are still providing people to manage your system components that are assessed against the 110 controls that govern the protection of CUI. They also likely have you tied into a remote monitoring and management (RMM) tool and other solutions. Per the proposed rule once it goes final and if this doesn’t change (Highly unlikely to) “If an OSA utilizes an ESP, other than a Cloud Service Provider (CSP), the ESP must have a CMMC certification level equal to or greater than the certification level the OSA is seeking.”.
If you’re only handling FCI then complete your 17 requirements and submit your 110 into the SPRS?
Say what?! I’ve seen this not once, not twice, but several times up to this point. Let’s walk over to Defense Federal Acquisition Regulation Supplement (DFARS) for a moment. But first, it is worth pointing out that the DFARS is a DoD supplement to the FAR and the DFARS 252.204-7012 is around protecting Controlled Unclassified Information (CUI) and the 7019 clause is the requirement for submission to the Supplier Performance Risk System (SPRS). Under the 7012 clause it references the implementation of NIST SP 800-171 as the baseline for safeguarding covered defense information. Yeah, yeah, I know…”but Dave, what about 32 CFR, DFARS 252.227-7013, 252.239-7010, FedRAMP, and other items.” I’m writing a blog post not a book.
Federal contract information (FCI) “means information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government.” CUI is “information the Government creates or possesses, or that an entity creates or possesses for or on behalf of the Government, that a law, regulation, or Government-wide policy requires or permits an agency to handle using safeguarding or dissemination controls.” Now the kicker is “All CUI in possession of a Government contractor is FCI, but not all FCI is CUI.”
For the purposes of the blog post we’re not going to get into distinguishing between when FCI is considered CUI or not and just work with the assumption that you’re only handling FCI that isn’t deemed CUI. In this instance does DFARS apply to you if only handling FCI and beholden to just the FAR 52.204-21 basic safeguarding requirements? The answer is no, and no you should not submit a score up to the SPRS. By submitting a score into SPRS your attesting to your level of compliance with NIST SP 800-171 not to the basic safeguarding requirements which are only 17 of the 110 controls.
For those that have read this looking for clarifications, I hope you enjoyed the content. For those that spread the misinformation I have a little Bill Engvall for you and will close with “here’s your sign”.

Did you know KTL Solutions offers a no-cost CMMC consultation? Click here to learn more.


































