Originally posted in the Microsoft Public Sector Blog by Justin Orcutt, Jan 11, 2022
In This Article:
- On November 4th, 2021, the Department of Defense (DOD) released several changes to the Cybersecurity Model Certification (CMMC).
- CMMC is intended to standardize and raise the bar for cyber security in the Defense Industrial Base (DIB) using CMMC third-party assessment organizations (C3PAOs) and self-assessments to enforce security requirements.
- While more rules and refinement for CMMC 2.0 are to come, companies are preparing now and using CMMC 2.0 as a mechanism to help improve security. For companies that are pursuing CMMC, we see a variety of practices emerging to support a successful upcoming certification.
What is CMMC 2.0, and why is it coming out now?
Following concerns of a lack of safeguards surrounding the loss of Federal Contract Information (FCI) and Controlled Unclassified Information (CUI) in the Defense Industrial Base (DIB), the DOD introduced Cybersecurity Maturity Model Certification CMMC in 2019 and reinforced the requirements with the Defense Federal Acquisition Regulation (DFARS) interim rule, followed by the release of CMMC 1.0.
The CMMC framework was intended to standardize and raise the bar for cyber security in the U.S. Defense Industrial Base (DIB) using a carefully outlined set of practices and an assessment.
Though CMMC 1.0 was never fully implemented across the DIB, the DFARS interim rule accumulated over 850 public comments. In addition, the National Defense Authorization Act (NDAA) 2021 directed the Government Accountability Office (GAO) to audit CMMC Project Management Office (CMMC PMO) and CMMC Accreditation Body (CMMC- AB). These two activities demonstrated the impact of CMMC was significant, and the industry was interested in protecting the supply chain but needed a different approach.
The result of all the comments was the November 2021 announcement of an updated, refined version of CMMC 1.0, aptly dubbed CMMC 2.0.
While the exact timeline is still up in the air, the DOD’s November 2021 announcement is the first step in rolling out their update into CMMC 2.0, and the final version will be further refined, published, and required for DIB suppliers within the next nine to twenty-four months into 2023. These activities are the result of the rule making process starting over to incorporate CMMC 2.0 into law.
The newly published scoping guide for CMMC 2.0 highlights the range of assets that need to be documented and protected. While not all controls will apply to all assets it is important for suppliers to understand CMMC requirements and how those requirements apply to specific assets. Both versions of CMMC were focused on protecting CUI, however, the new scoping guidance for CMMC 2.0 makes it clear how to scope your environment.
The regulatory environment has become increasingly complex, with varying industry and geographical standards that are constantly evolving. The complexity of regulations makes it challenging for organizations to know the specific actions they can take to meet their compliance requirements. To keep pace with the ever-changing regulatory landscape companies need to understand shared responsibilities with suppliers but also implement best practices for their industry. Microsoft’s products are certified against various regulatory requirements. Microsoft also provides tools and management to help companies stay ahead of these changes.
What is new in CMMC 2.0?
CMMC 1.0 Levels 3-5 were based on National Institute of Standards and Technology Special Publication (NIST SP) 800-171 which was also what the DFARS clause 252.204-7012 required. The DFARS 252.204-7012 clause was a preexisting clause in contracts requiring suppliers who handle CUI to adhere to the NIST SP 800-171. Since the DFARS clause 252.204-7012 was published, suppliers in the DIB have had to maintain essential cybersecurity and report incidents within 72 hours.
CMMC 1.0 built off the foundation of DFARS 252.204-7012 and created a tiered system of practices with five levels to represent basic to advanced/progressive cyber maturity and hygiene. But unlike DFARS, CMMC 1.0 did not allow for self-attestations of compliance or Plans of Action and Milestones (POA&Ms) to demonstrate intent to become compliant. Instead, suppliers had to be certified at the appropriate maturity level by an independent CMMC Third-Party Assessor Organization (C3PAO). If a supplier wanted to certify at one of the five levels, they would need to be validated by an independent C3PAO and have all practices implemented at the level they were pursuing. CMMC 1.0 was a rigid framework that lacked the flexibility provided in CMMC 2.0.
The most obvious change between CMMC 1.0 and CMMC 2.0 is that the total number of assessment levels has gone from five to three: Level 1 (Foundational), Level 2 (Advanced), and Level 3 (Expert). The number of controls under each level has also decreased.
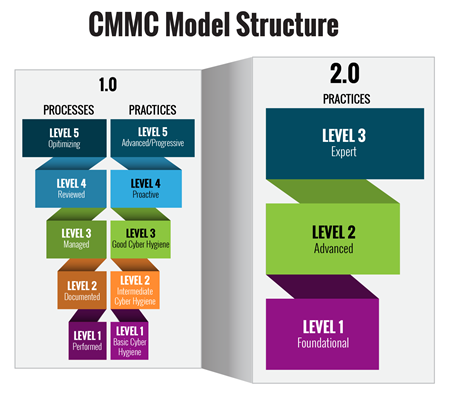
Figure 1: Key Features of CMMC 2.0 from Office of the Under Secretary of Defense Acquisition & Sustainment – Cybersecurity Maturity Model Ce…
Each level is based on required practices and controls, and in a tiered manner, each level builds on the the previous level.
At level 1, organizations will still need to demonstrate basic cyber hygiene across 17 practices which represent the basic safeguarding requirements under FAR 52.204-21 which has been in place since 2016.
At level 2, organizations will have to demonstrate they have implemented the requirements of NIST SP 800-171, the same controls that were already required under the preexisting DFARS 252.204-7012 clause.
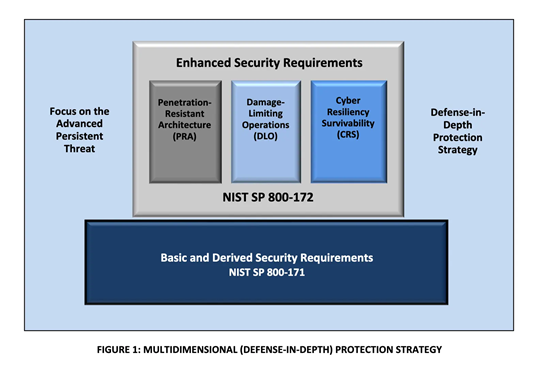
At level 3, contractors will need to demonstrate compliance with a subset of NIST SP 800-172. Specifically which of the requirements from NIST SP 800-172 are still to be defined. However, NIST SP 800-172 was designed to help protect against Advanced Persistent Threat (APT) actors which are currently targeting the US Department of Defense supply chain. NIST SP 800-172 provides the foundation and controls for a defense-in-depth protection approach.
Aside from the controls within each of the three levels, there are additional practices that can be applied to further help build cyber resilience.
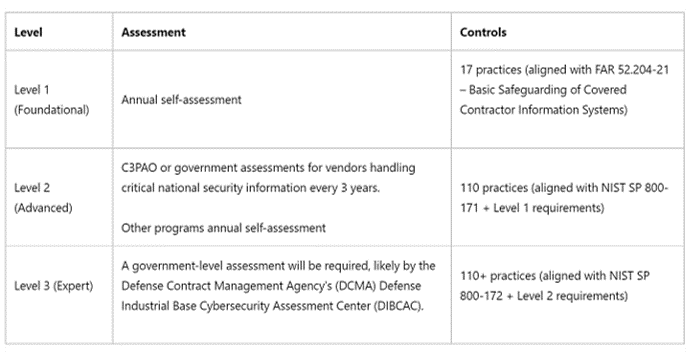
Suppliers may have a choice between Self Assessments, C3PAO Assessments, & Government Assessments.
In CMMC 2.0, Level 1 suppliers are now allowed to self-assess. This is similar to what is allowed under FAR 52.204-21 which are the Basic Safeguarding of Covered Contractor Information Systems. The key difference is executives will now be the ones to have to certify to the level of compliance within their business.
Level 2 suppliers have two internal tiers for assessments. Some suppliers or programs, like Level 1, will be able to complete annual self-assessments. However, Level 2 suppliers who handle “critical national security information,” (estimated to be around 40,000+ suppliers) will be required to undergo assessments by C3PAOs.
The type of CUI that a Level 2 supplier handles will determine whether they will be required to have an assessment completed by a C3PAO or complete a self-assessment for their Level 2 compliance. If, for example, a supplier provides supplies to critical weapons or defense systems, they will likely need to obtain a C3PAO assessment.
Level 3 suppliers will be required to undergo a government-led assessment every three years. While the details of which agency will be handling these assessments, it is speculated that it will be the Defense Contract Management Agency’s (DCMA) Defense Industrial Base Cybersecurity Assessment Center (DIBCAC).
While the DOD is moving forward with CMMC 2.0, other departments across the Federal Government dealing with CUI are developing their own plans for data protection. There will likely be a new FAR rule to outline, and update required protections for any third party to come in contact with CUI.
There will be a pathfinder program for the Department of Homeland Security’s (DHS) contractors. They are not included in the scope of CMMC and will require a more stringent set of controls and assessments. According to the DHS, which launched a pathfinder in the summer of 2021 with CMMC-like language, the “CMMC 2.0 might leave gaps in contractor cybersecurity”, especially with the existence of additional waivers, POA&Ms, and self-attestations.
For a simple reference, see this chart below:
Perhaps most notably, CMMC 2.0 allows the use of waivers and POA&Ms.
A central sticking point for DIB suppliers under CMMC 1.0 was the inability to demonstrate the intent for compliance through a Plan of Actions and Milestones (POA&M) — a document which identifies gaps and developing project plans set to address these gaps.
Under CMMC 2.0, the DOD has announced that it intends to allow contractors to use POA&Ms to achieve certification compliance as a prerequisite, provided specific deadlines for completing the remaining items are included.
While the specific controls and circumstances where POA&Ms will be allowed have not been outlined, they will be aligned with the NIST SP 800-171 and the DoD Assessment Methodology, meaning we can extrapolate from the existing publication what the future publication will likely contain.
Certain high-value items will be too important to security to include in a POA&M, and therefore cannot be included in a POA&M.
If your environment is not currently constructed to handle CUI, you’ll have to do the foundational work to ensure that it can. Some of the highest-value activities that likely won’t be allowed on a POA&M include:
- NIST SP 800-171 requires user authorization, processes, transactions, on-premises, wireless connections, and encryption which may seem simple they can be deceptively complicated to implement. They often require several behind-the-scenes steps that are critical to security. (Moreover, there are nearly two dozen of these controls; see Access Controls (AC) 3.1.1, 3.1.2, 3.1.12, 3.1.13, 3.1.16, 3.1.17, & 3.1.18.)
- Requirements on training span from “awareness” to “skills” within your technical and security teams are enormous in scope. (Awareness and Training (AT) 3.2.1 & 3.2.2)
- High-value requirements around audit records require businesses to monitor and document system audit logs (Audit and Accountability (AU) 3.3.1) and correlate audit record review, analysis, and reporting processes for investigation and response to indications of unlawful, unauthorized, suspicious, or unusual activity. This control (AU 3.3.5) is challenging to centralize to a SIEM.
- Requirement Media Protection (MP) 3.8.3 requires suppliers to sanitize or destroy system media containing CUI before disposal or release for reuse.
- Requirement Risk Assessment (RA) 3.11.2 requires that suppliers scan for vulnerabilities in systems and applications periodically. Once vulnerabilities are identified this means that action can be taken to remediate those vulnerabilities.
What does the release of CMMC 2.0 mean for the DIB?
Unfortunately, there is little information about CMMC 2.0, and we expect the DOD will release more as the process unfolds.
For now: plan to be certify compliance ready by mid-2023. To certify compliance, you may need a C3PAO assessment, government led assessment or qualify for a self-assessment.
The Pentagon recommends suppliers (especially those pursuing CMMC Level 2 and above) follow the NIST SP 800-171 framework and prepare for CMMC assessment. Most DOD suppliers are already required to comply with NIST 800-171, but additional documentation may be required.
When CMMC becomes incorporated into law after the rule making process, there will be a surge of the 40,000 Level 2 suppliers who will be searching for a C3PAO to complete their assessment as soon as possible. Many of these 40,000 suppliers have already been preparing for CMMC 1.0.
In addition, there are several reasons to expect many businesses will get assessed as soon as possible:
- The DOD may offer incentives to contractors that voluntarily get assessed while the rulemaking is ongoing.
- Contractors with a CMMC 2.0 certification will be first in line to renew or obtain new contracts with the DOD.
- Like the Gramm-Leach-Bliley Act or the Sarbanes–Oxley Act process, publicly-traded companies may pursue CMMC 2.0 to demonstrate how they prioritize cybersecurity and build trust within their communities.
If your organization handles CUI and is part of building war fighting capabilities, you will likely be required to find a C3PAO to achieve CMMC certification. This means that while you currently have a requirement for compliance with NIST SP 800-171 as part of DFARS 252.204-7012 you will now be required to be assessed by a C3_A). To prepare for CMMC 2.0 we recommend you continue to align your security program to NIST SP 800-171 as well as getting executive buy-in early: proper planning will be vital to achieving CMMC 2.0 in a reasonable timeframe.
CMMC 2.0 Preparation Recommendations
1. Centralize compliance monitoring
DOD suppliers have been preparing for CMMC 1.0 for around two years while also pursuing compliance with DFARS 7012 and NIST SP 800-171 for even longer. While the controls and practices may change, these practices that we’ve seen emerge across the DIB will help suppliers stay ahead of the DOD’s changing requirements. This is not intended to be a comprehensive list rather a snapshot of a few recommended practices. Leverage technology to centralize the process of assessing and providing continuous monitoring of compliance.
One of the most strenuous activities required by CMMC is the necessity of implementing a continuous monitoring program for compliance. Compliance is not a project with a start and end date, rather it is an ongoing responsibility and CMMC will assess and certify whether suppliers are meeting that responsibility. If a supplier doesn’t already have documentation or programming in place, now is the time to start.
Use a compliance management tool that works for you. The best programs will handle continuous monitoring, map controls, and come with regulatory updates, but it’s also important for any program you implement to be user-friendly: look for a program that has dashboards for easy viewing, options for scalability, and intuitive interfaces.
Microsoft’s Compliance Manager comes with prebuilt CMMC templates and hundreds of others that your business can use to easily complete control mapping to simplify your compliance journey. Compliance manager can be used in conjunction with Defender for Cloud apps which can assess the compliance of cloud apps to help prevent data leaks to non-compliant apps and limit access to regulated data.
To get a single pane of glass for gathering and managing security controls beyond CMMC suppliers can also leverage the Azure Security Benchmark and Azure Security Center to get recommendations for improvement actions.
2. Protect data using labeling and access rules
Protecting CUI is core to CMMC to prevent unauthorized users from gaining access to this sensitive information. Suppliers traditionally have data spread out across the organization and determining where CUI is located can be difficult. This data is not always marked, making it difficult to manage. It is important to gain an understanding of what data exists, how to protect that data, how to prevent loss and how to govern that data moving forward.
Microsoft Information Protection can help suppliers identify data, apply protections, protect data and apply retention or deletion rules so the data lifecycle can be managing. Scanning for sensitive data and establishing data classifications can be helpful first steps to helping set the scope of an assessment. Once sensitivity labels are established based on business requirements policies can be established on top of those labels to protect the document contained within those files.
3. Extend SOC visibility into ERP systems and all endpoints, including IoT.
Most DIB suppliers avoid combining the CUI they handle with their enterprise resource planning (ERP) system, but as ERPs are integral to business operations, this isn’t always possible. When ERPs contain a significant amount of sensitive data, its protection becomes vital.
While identity access management can prove effective, it doesn’t provide advanced protection like bypassed security controls or privilege escalation. Extending Security Operation Center SOC visibility to your business’ ERP may help alleviate these needs and raise the bar to meet CMMC 2.0 requirements.
Microsoft’s recently-developed Continuous Threat Monitoring program for ERPs which normalizes log data, allowing for increased visibility and insight into your system’s security, catching incidents faster, and analyzing them with higher quality.
Additional steps should be made to give the SOC has visibility into all asset categories within CMMC scoping guidance which includes Controlled Unclassified Assets, Security Protection Assets, Contractor Risk Managed Assets, and Specialized Assets (IoT or Industrial Internet of Things, operational technologies, restricted information systems, and test equipment).
4. Develop standard landing zones for teams to build from as a starting point.
Zoning will likely be helpful towards demonstrating CMMC compliance. By segmenting infrastructure into logical groupings that have the same communication security policies and requirements, some of the risk of having open networks can be alleviated.
You can even effectively utilize landing zones, policy, benchmarks, and CMMC controls within your security center to make the process simpler. Azure Landing Zone makes it not only possible, but simple to leverage all of your business’ cyber security against CMMC.
5. Correlate data to help provide better inputs for insider threat programs.
The DoD Assessment methodology specifically calls out data correlation as one of its most high-value controls because it’s particularly time consuming, difficult, and requires a level of sophistication in a supplier’s cyber security program.
Fortunately, getting a head start may alleviate some of the pressure on organizations seeking Level 2 or 3 CMMC compliance.
Your business should seek to improve response speed with the data you already have at your fingertips. One option we recommend is central logging and monitoring in the cloud. It has several benefits, the least of which is improved use of Artificial Intelligence to improve response speed. Microsoft Sentinel can also help lower response times. Read our Quick Start Guide to get off the ground and reduce your blind spots. Contractors concerned about insider risks can also leverage tools like Insider Risks Management to get visibility on various risks like data spillage, confidentiality violations, insider trading or regulatory violations.
6. Extend incident response or forensic capabilities by centralizing and retaining logs for more extended periods.
System logs are numerous and tedious to track, maintain, and analyze, but they’re the key to correlating data, raising cybersecurity maturity, and getting CMMC right the first time. Moving logs to a central location and storing them for longer periods of time can directly impact incident response time and capability. Collecting logs on endpoints, enterprise applications and specialized assets are part of a robust security program.
Today, Microsoft customers can extend log retention for up to 10 years within Advanced Audit, and by discontinuing the use of log storage. As businesses in the DIB continue the conversation around maximizing the effectiveness of information, we recommend taking steps internally and taking notes.
7. Leverage community training to help upskill staff.
Several trainings are free or available at a low cost for DIB suppliers. Staff can participate in Procurement Technical Assistance Centers, Manufacturing Extension Partnerships or programs like Incumbent worker training which is available through Connecticut Center for Advanced Technology.
Microsoft also offers hundreds of hours’ worth of educational material through Microsoft Learn, where businesses can train and certify individuals. As another option, employees can participate in virtual training days. For yet another learning path, annual conferences, like Microsoft Build or Microsoft Ignite, are an excellent source of information.
In addition, our ecosystem of partners provides additional training opportunities in either a private or public format so you can pick what is best for you.
The regulatory environment has become increasingly complex, with varying industry and geographical standards that are constantly evolving. The complexity of regulations makes it challenging for organizations and IT administrators to know specific actions they can take to meet their compliance requirements. Companies must adapt to this ever-changing landscape. Microsoft’s products are aligned to various regulatory requirements to help you stay ahead of these changes.
To help along your compliance journey we have created a CMMC Product Placemat to provide an interactive view on how Microsoft products and services can help satisfy requirements for CMMC. The placemat can be helpful to visualize products and services you can leverage as part of your overall compliance program.
To learn more about how Microsoft can help you on your CMMC journey please visit https://aka.ms/cmmc, follow our CMMC Acceleration program, engage in our tech community or contact us at CMMC@microsoft.com .
To learn more about CMMC scoping guidance please visit the official scoping guide for Level 2.



































