The Department of Defense (DoD) announcement on November 4 “Strategic Direction for the CMMC Program” provided new guidelines for the Cybersecurity Maturity Model Certification (CMMC). Our KTL webinar on November 10 helped to clarify these changes and answer questions for those in the Defense Industry Base (DIB).
CMMC 2.0
CMMC is a key component of the Department’s expansive DIB cybersecurity effort. The DIB is the target of increasingly frequent and complex cyberattacks by adversaries and non-state actors. Dynamically enhancing DIB cybersecurity to meet these evolving threats, and safeguarding the information that supports and enables our warfighters, is a top priority for the Department.
“CMMC 2.0 will dramatically strengthen the cybersecurity of the defense industrial base,” said Jesse Salazar, Deputy Assistant Secretary of Defense for Industrial Policy. “By establishing a more collaborative relationship with industry, these updates will support businesses in adopting the practices they need to thwart cyber threats while minimizing barriers to compliance with DoD requirements.”
Summary of Changes
The revised requirements in CMMC 2.0 include updates to the model, assessments and implementation.
Streamlined Model
- Focused on the most critical requirements: Streamlines the model from 5 to 3 compliance levels
- Aligned with widely accepted standards: Uses NIST cybersecurity standards
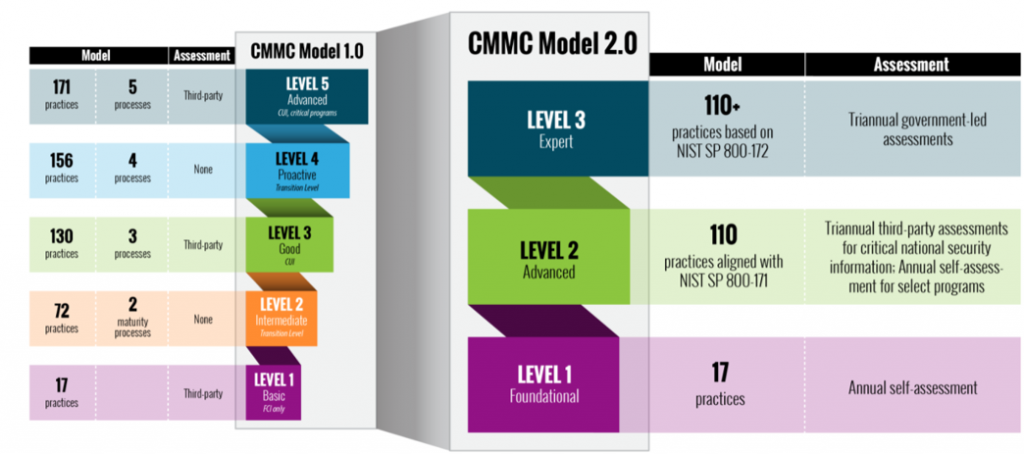
Reliable Assessments
- Reduced assessment costs: Allows Level 1 and a subset of Level 2 companies to demonstrate compliance through self-assessments
- Higher accountability: Increases oversight of professional and ethical standards of third-party assessors
Flexible Implementation
- Spirit of collaboration: Allows companies, under certain limited circumstances, to make POA&Ms to achieve certification
- Added flexibility and speed: Allows waivers to CMMC requirements under certain limited circumstances
CMMC Assessments
CMMC 2.0 implements tiered assessment requirements based on the sensitivity of the information shared with a contractor. Upon implementation of CMMC 2.0:
- Contractors who do not handle information deemed critical to national security (Level 1 and a subset of Level 2) will be required to perform annual self-assessments against clearly articulated cybersecurity standards.
- Contractors managing information critical to national security (a subset of Level 2) will be required to undergo third-party assessments.
- The highest priority, most critical defense programs (Level 3) will require government-led assessments.
Plan of Actions and Milestones (POA&Ms)
With the implementation of CMMC 2.0, the Department intends to allow companies to receive contract awards with a Plan of Action and Milestones in place to complete CMMC requirements.
The Department’s intent is to specify a baseline number of requirements that must be achieved prior to contract award, in order to allow a remaining subset to be addressed in a POA&M within a clearly defined timeline.
Key Points
As stated by Buddy Dees, Director, CMMC Program Management Office during the CMMC Accreditation Board Town Hall on November 9, “DIB Companies are going to have to have processes in place in order to put their practices in effect.” Appendix E of NIST SP 800-171 references NFOs that should be reviewed since processes and policies are implied.
The publication of materials relating to CMMC 2.0 reflect the DoD’s strategic intent with respect to the CMMC program; however, CMMC 2.0 will not be a contractual requirement until the DoD completes rulemaking to implement the program. The rulemaking process and timelines can take 9-24 months. CMMC 2.0 will become a contract requirement once rulemaking is completed.
What should DIB companies be doing now to prepare?
Most cyber incidents start because of user error. Educate people about the importance of setting strong passwords, recognizing malicious links, and installing the latest security patches. Helpful materials and training videos are available through Project Spectrum. Here are five steps to increased cybersecurity you can begin to work on right away.
- Educate your team on cyber threats
- Implement access controls
- Authenticate users
- Monitor your physical space
- Update security protections
Additional Information
To view the KTL “CMMC News for the DIB” webinar in its entirety, you may access the video on our YouTube channel.
For more information on CMMC 2.0, contact us at info@ktlsolutions.com. We have experienced CMMC-RPs on staff ready to help.



































